- Zones (e,s-Wall)
- Trusted Zone Traditions
- Many personal security products divide the entire network into two main zones: Trusted and Unsafe. Trusted zone includes the computer under protection and (possibly) the local network (if any) and allows any network operations. These operations are expected safe because the zone is trusted. Unsafe zone is the all the other network, that is unknown and as the result unsafe. This principle works fine but it could be significantly improved by "Application's Zone" approach.
- Suppose that a computer has a number of applications (stand-alone or system dependant). The system itself (operation system) could be assumed as a special application too because it is independent participant of the network interaction providing disk and printer sharing and so on. Each of this application could have its own creation of zone safety.
- Application's Zone
- Consider several applications in terms of zone trust
- Internet Explorer (or another Web browser) needs to have the access anywhere inside the local network as all over the world too. There is no special trust difference between local and internet access of a web browser.
- Outlook (or another e-mail program) needs the access to correspondent mail (POP3/IMAP/SMTP) server only. It could be strange (as the result unsafe) for access anywhere else.
- Antivirus could obtain its updates only at the AV developers' site and nowhere else. For that reason, Antivirus's trust zone is only one host in the internet.
- As the result, Application's zone is more safe and reliable approach to protect your computer. It only expands the traditional method. If you suddenly want to use habitual zone method, you could create only one zone that fully enables only local network traffic and apply that zone to all the applications.
- Zone Override
- Zone override also expands the traditional point of view. It is usually to have a "panic button" to disable all traffic and (vice versa) a button to disable the guard temporarily (enable all traffic). "Zone Override" can significantly expand this approach. You can use a single zone to use with all the applications saving separate application-specific settings. If you set "Disable All" zone as Zone override you will block all the network traffic. "Enable All" disables all the traffic and stops the guard. However, you could set "LAN Only" zone as Zone override and fill free only in the local network. More than that, you could use temporarily any zone including custom created one to trust temporarily in your "maternal" computer only.
- Zone Manager
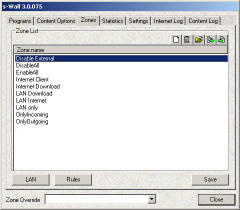 x-Wall has Zone manager to create, delete, import, export or modify zones. Zones are most powerfull opportunity for applications' internet access control. Right mouse button menu is available. x-Wall has Zone manager to create, delete, import, export or modify zones. Zones are most powerfull opportunity for applications' internet access control. Right mouse button menu is available.- First time x-Wall starts after the installation, it detects windows network configuration. It tries to detect all the present LAN setting and to configure LAN dependent zones. x-Wall initially assumes that all the LAN access (via all currently installed adapters) is safe. There are two buttons helping to make group rule/zone changing (for advanced users)
- LAN button helps you to override initial settings retrieved from configuration of LANs that your computer is connected. Pressing the button x-Wall collects the entire present network configuration and makes separate Rule for each LAN adapter. You are given a chance to tune these rules. For example, your computer is connected to more than one LAN simultaneously. Not all the LANs are trusted (consist of trusted computers). The dialog allows you to modify the rules for each the LAN separately. After all the rules are configured, the automated rule-replace procedure will be started. x-Wall examines each zone and finds the zones containing NET rules. The rule name starting with NET indicates the LAN rule. If a zone contains the NET named rule, all those rules will be deleted and the new NET rules you have just edited will be placed at the head of the zone. Be careful, it is fully automated procedure. You can backup all the x-Wall's setting using Save/Restore Setting procedure from Programs menu
- Rule button is used to update rules with the same name in the all zones. Firstly, all the unique named rules from all the zones are collected. Than you are shown the edit zone dialog with all these rules and you have chance to make correction. After that x-Wall will iterate through all the zones and will replace all rules with matched names with the new parameters you have just entered.
- "System" Application
- Windows itself could be assumed as the application with the special name System (without correspondent EXE file of course). System application performs network operation as any other application and could be controlled by x-Wall. As the System network activity concerns with disk/printer sharing x-Wall can perform the art control under the sharing. Majority of the network security manual recommends to disable disk sharing as the most dangerous point of possible unauthorized access. However if you really need to give somebody the access your disk shares you can provide yourself with the security using x-Wall. In that case you should use zones and give the access to the disk share for trusted computers only.
- Zone Explanation
 Zone is a set of rule and options to make the decision of permission or prohibition the internet access. Each time an application accesses to internet, it has the parameters of the connection trying to perform (address and port of the remote computer, used protocol and interaction (in or out) direction). Each time an application trying to access the internet x-Wall compares the connection parameter with correspondent zone (separate application's zone or zone override if any). x-Wall should match the zone with connection parameters and pass or stop the internet access. Zone is a set of rule and options to make the decision of permission or prohibition the internet access. Each time an application accesses to internet, it has the parameters of the connection trying to perform (address and port of the remote computer, used protocol and interaction (in or out) direction). Each time an application trying to access the internet x-Wall compares the connection parameter with correspondent zone (separate application's zone or zone override if any). x-Wall should match the zone with connection parameters and pass or stop the internet access.- Zone Assignment
- Each time a new application tries to have the internet access you will be notified via special dialog with application details for making correct decision of suitable application's zone. The "default zone" from Settings tab is initially used. You can change it by that dialog or any time later. However, the main question is still the same. Which zone should I use?
- The answer in not so exact, but is useful. Choose the most suitable zone by name. (see Zone tips)
- To define exact answer you should know the applications as its developer and have to its behavior in details. It is impossible for a user, but correct zone setting is possible indeed.
- Usually, you will find the suitable application zone at the second iteration maximum (in 99% of cases).
- It is impossible to perform that kind of security actions formally and automatically. In that case, "press button to full secure" applications would have been available. The main principle is enabling the minimal internet access you need only. In any case, zone (security) tuning is the iterative process with attempts and error corrections (see myths and legends).
The main principles are: - Do not enable the internet access to unknown application.
- Keep internet access at the minimal sufficient level.
- Always check internet access log to prevent security holes
- Remember that any security solution is only a tool in your hand without any magic
- Suggest the next paradigm.
- Disable maximum number of applications (including system services and the System itself)
- Find that something is not working
- Check the Log
- If you find that something is not working try to set another (more suitable) zone.
- Imagine the application something.exe is detected as internet access candidate. If you do not understand what it is, or the application appearance is not caused by your actions choose disable all. Verify that all that your vitally internet access is enough for you. If something is not working try LAN only zone.
- In other words, increase the internet access rights gradually until everything will be good enough.
- Do not think that extremely complex, it is the single way to provide yourself with real security.
- How Zone Works
- To use predefined zone you don not need to understand zone details. Simply choose suitable zone for an application or for Zone Override. Zone details will be needed only for zone edit or custom zone creation.
- Zone is a set of rules and zone result saved under zone name. Each rule consists of the rule's name, set of parameters (as connection parameters) and rule's result. To make pass/stop decision x-Wall iterates throw the zone's rule list (if any) and compares the connection parameter with the rule parameter. If defined rule's parameters matched the connection parameters, the zone result (and result application permission) will be equal to the matched rule result. If no rules are matched with the connection parameter, zone result will be used to make application stop/pass decision.
- The sample LAN+Internet Zone. An application is trying to access computer at 123.456.789.123 address, port 80, protocol TCP and direction outgoing and it uses the zone LAN+Interent. Let us walk through the rules
- Local Enable. Rule's address/mask is 127.0.0.1/255.255.255.0. It means the address diapason from 127.0.0.0 to 127.0.0.255. Value of 255 in the mask means exact part of address; value of 0 in the mask means any from 0 to 255. It is simplified but correct. Our address (123.456.789.123) is not matched with rule's address interval. As the result the whole rule is not matched and we should try with the next rule
- LAN 1. LAN rule (if any) depends on your local network connections. It could differ from the sample.
Assume your first LAN (LAN adapter) has the address 10.0.1.4/255.255.255.0. It is not matched with our remote computer. As the result rule is skipped. - DNS Enable rule does not contain address/mask conditions defined but has the port (53) defined. It is not matched to desirable port (80). As the result rule is skipped.
- DHCP Enable is skipped too for the same reason.
- EnableOut rule does not have any parameter defined expect direction parameter. We are trying to perform outgoing connection, which is matched with out direction. The rule result is enabling. As the result, the access will be granted.
- If the last rule is not matched, the whole zone result (disable) will be used and application's access will be stopped.
To obtain IP address from name of a site you can fill the host field with the name of a site and press "Address by name" button. IP address will be filled automatically. - Composing Zones (for advanced users)
- Before the composing your own zone you should be sure that there are no predefined zone suitable for you and there are no zones could be corrected to be suitable for you. To correct the existent zone is much simpler than create your own from scratch.
- You could follow one from two paradigms
- Choose the zone result equal to disable and add rules enabling some hosts, protocols or directions.
- Choose the zone result equal to enable and add rules disabling some hosts, protocols or directions.
In other words, you should decide you mostly permit the access or prohibit it. Then use an application performing the test, check the Log and play with the rules ... - Always remember that there are some well-known services (DNS, DHCP etc) could be required for the new zone.
|
 x-Wall has Zone manager to create, delete, import, export or modify zones. Zones are most powerfull opportunity for applications' internet access control. Right mouse button menu is available.
x-Wall has Zone manager to create, delete, import, export or modify zones. Zones are most powerfull opportunity for applications' internet access control. Right mouse button menu is available. Zone is a set of rule and options to make the decision of permission or prohibition the internet access. Each time an application accesses to internet, it has the parameters of the connection trying to perform (address and port of the remote computer, used protocol and interaction (in or out) direction). Each time an application trying to access the internet x-Wall compares the connection parameter with correspondent zone (separate application's zone or zone override if any). x-Wall should match the zone with connection parameters and pass or stop the internet access.
Zone is a set of rule and options to make the decision of permission or prohibition the internet access. Each time an application accesses to internet, it has the parameters of the connection trying to perform (address and port of the remote computer, used protocol and interaction (in or out) direction). Each time an application trying to access the internet x-Wall compares the connection parameter with correspondent zone (separate application's zone or zone override if any). x-Wall should match the zone with connection parameters and pass or stop the internet access.